11 October 2022
Updated: 28 November 2023
What Is Bitcoin (BTC)? — First Blockchain and Cryptocurrency

Table of contents
Table of contents
You might be wondering how does Bitcoin work? There are actually a lot of ingenious technologies bundled together to make the network run smoothly. In this article, we'll look at the basics of Bitcoin code, security, and transactions.
The Bitcoin protocol was first announced on October 31, 2008, when Satoshi Nakamoto, the anonymous founder(s) of Bitcoin, sent the Bitcoin whitepaper to the Cypherpunk email list. Just over two months later, around January 3, 2009, the first block in the Bitcoin blockchain was mined and the Bitcoin protocol came to life. Today, the Bitcoin protocol is responsible for securing a network of close to $1 trillion in digital assets.
The Bitcoin Protocol Explained
Before we jump into the technology that has enabled this network to flourish, it's important to understand how Bitcoin is unique from traditional payment systems. Adoption is happening at a global scale - and national governments taking a pro-Bitcoin stance as we see with Bitcoin adoption in El Salvador.
Decentralized Network
What makes Bitcoin unique from a bank is its decentralization. Rather than relying upon a central database to record transactions, Bitcoin is one example of distributed ledger technology. A decentralized network of computers (nodes) help to verify that transactions are legitimate. This removes the element of trust and also creates a censorship-resistant network that allows anyone to make transactions without any obstacles.
Proof of Work Consensus
Bitcoin was the first blockchain network to introduce Proof of Work - a blockchain consensus mechanism in which powerful computers compete to solve a mathematical equation in order to receive block rewards (BTC in this case). This process is known as cryptocurrency mining - the security mechanism that protects the Bitcoin protocol from double spend attacks and other threats.
BTC - Native Currency of Bitcoin
Each unit of currency on the Bitcoin blockchain is referred to as a Bitcoin, which is often referred to by its ticker symbol: BTC. The network is designed so that only 21 million BTC will ever exist - with the last expected to be mined (created) around 2140. Because Bitcoin is a public blockchain network, the total number of BTC in existence can be verified by anyone at any time. The rate of BTC generated through cryptocurrency mining is programmed to cut in half every four years (known as "the halving" or "the halvening"). This makes BTC a deflationary asset, unlike fiat currencies or even many other cryptocurrencies.
Bitcoin Source Code
Easy accessibility is one attribute that has led to mass adoption of the Bitcoin protocol. Satoshi Nakamoto launched Bitcoin Core as open source software, which enables blockchain developers to continuously release new updates that improve protocol functionality.
The original Bitcoin Core source code is written in C++, and the up-to-date implementation can be found on GitHub. C++ is not only used on the Bitcoin protocol but has also become one of the most popular blockchain programming languages across other protocols. This programming language supports tight control of memory and CPU usage. It also enables nodes to quickly validate and propagate blocks, which means transactions are processed efficiently.
As Bitcoin became more popular, new clients written in other programming languages have been released. Today blockchain developers also have the option to build Bitcoin applications using Python, Golang, Java, or Rust.
Unspent Transaction Output (UTXO)
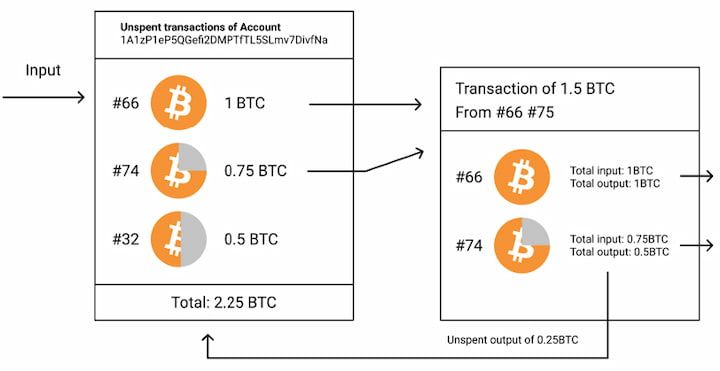
BTC is the Bitcoin protocol’s native coin and used in all network transactions. To organize BTC transactions, the Bitcoin protocol introduced the world’s first blockchain (one variety of distributed ledger technology). More specifically, Bitcoin uses an unspent transaction output (UTXO) model as a way to keep track of how funds move and to prevent the double spending problem. It’s crucial to understand that each UTXO can only be spent once. When one user spends a UTXO, one or more new UTXO is created.
Let’s say Bob has 1.2 BTC in his Bitcoin wallet. He wants to send 1 BTC to Alice. The network needs to recognize that Bob's wallet contains at least 1 BTC before the transaction can be processed. If Bob's wallet doesn’t contain at least 1 BTC, then it should be impossible for him to send 1 BTC to Alice.
In the UTXO model, one or multiple unspent outputs may be added together to reflect the total amount of funds that belong to one user. In our example, Bob might have one UTXO worth 0.5 BTC and another worth 0.7 BTC, equaling to the total amount of funds in his Bitcoin wallet. When sending 1 BTC to Alice, Bob actually needs to send the entire amount of both UTXOs (1.2 BTC). Bob then receives one new UTXO containing 0.2 BTC. Meanwhile, Alice receives one new UTXO containing 1.0 BTC.
Bitcoin Script & Opcodes
As discussed above, Bitcoin open source software (known as Bitcoin Core) is written in C++. However, the Bitcoin protocol actually uses another programming language called Bitcoin Script to give Bitcoin Core instructions on how each UTXO can be spent. At its core, this is the technology that determines how the Bitcoin Protocol actually works. The majority of users don’t actually need to learn Bitcoin Script. This is because both Bitcoin wallets and other applications complete Bitcoin Script processing behind the scenes automatically. Nonetheless, it’s good to understand what Bitcoin Script is and why it’s so important.
Bitcoin Script uses a system of operation codes (better known as Opcodes). Essentially, opcodes are commands which tell nodes in the Bitcoin network how to process any transaction request. Each opcode starts with the prefix “OP_” and is followed by a specific command. For example, OP_CHECKSIG is used as a mechanism for verifying that the sender of a transaction applies the correct digital signature. No matter whether a user wants to send a standard transaction or create a custom transaction script, Bitcoin Script and opcodes are required components of this process.
Bitcoin Private Keys
To keep user funds secure, the Bitcoin protocol makes use of asymmetric encryption. In this system, users can generate private keys (also known as secret keys) as part of a private-public key pair. Private keys are meant to be kept secret, and public keys can be shared publicly to receive BTC transactions. Only a user who has access to the matching Bitcoin private key can spend funds (unlock UTXO) that are sent to a corresponding public key. In this way, a public key is comparable to a bank account number. A private key is comparable to a passcode for a bank account. The main difference is that the private key is an incredibly large number— so enormous that the odds of guessing the correct private-public key pair combination are practically zero.
The security of Bitcoin private keys is supported by Elliptic Curve Cryptography (ECC) and cryptographic hash functions. These mathematical concepts are applied to provide two major benefits to users. First, users can share their public key with anyone in the network as a way to receive payments. Given the public key, it's practically impossible to reverse engineer the private key. Second, users who want to send BTC transactions on the network can use their private key to create digital signatures. A digital signature functions similarly to a one-time passcode for identity authentication. It enables the recipient of a transaction or anyone else on the network to mathematically prove with 100 percent certainty that a specific Bitcoin private key provided the signature. Furthermore, the private key is never revealed to the network in the process.
Bitcoin Wallets and Addresses
Like other cryptosystems using public key cryptography, we know that Bitcoin supports the generation of private-public key pairs. However, it actually takes this process a step further. While users can receive funds via a public key, they can use a Bitcoin wallet address (also known as a public address) instead to receive BTC transactions. A public address is created from a corresponding public key using two hashing algorithms: the Secure Hash Algorithm 256 (SHA-256) and the RACE Integrity Primitives Evaluation Message Digest 160 (RIPEMD-160). Public addresses are more widely used thanks to the security provided by this extra layer of encryption and the friendlier UX provided by a shorter alphanumeric string.
Each Bitcoin wallet comes with a private key and a corresponding public address by default (as well as a public key). A commonly-used analogy is to think of Bitcoin wallets as key rings. Generally speaking, each Bitcoin wallet is designed to be able to store multiple key pairs. Users should be able to generate new key pairs whenever they want. Technically, BTC is never actually stored in a Bitcoin wallet. However, we can essentially think of a Bitcoin wallet as a user-friendly interface for storing, sending, and receiving BTC. A few popular types of Bitcoin wallets include desktop wallets, web browser wallets, hardware wallets, mobile wallets, and paper wallets.
Bitcoin Transactions
The Bitcoin protocol allows users to send different types of payments using Bitcoin Script. Three popular examples include Pay To Pubkey (P2PK), Pay To Pubkey Hash (P2PKH), and Pay To Script Hash (P2SH). Note that BTC is sent with each payment type, but the steps involved vary slightly.
Pay To Pubkey (P2PK)
When the Bitcoin protocol launched in 2009, Pay To Pubkey (P2PK) was an important payment type. At that time, it was the only payment type except for P2PKH. In 2009 and 2010, the network required users running nodes (known as cryptocurrency miners) to accept block rewards via P2PK transactions. Additionally, BTC mining software for CPUs supported P2PK. Although this payment type gained some early support, its usage faded due to the added benefits provided by using public addresses instead of public keys.
When a P2PK transaction is created and submitted to Bitcoin’s peer to peer network, the sender is sending funds from their own Bitcoin wallet to a public key (also known as pubkey for short) of another user. If the recipient wants to spend those funds (spend the corresponding UTXO) at any point in the future, they only need to prove they own the public key to which the funds were sent.
Pay To Pubkey Hash (P2PKH)
Along with P2PK, Pay To Pubkey Hash (P2PKH) was originally supported as a payment type when the Bitcoin protocol launched in 2009. P2PKH remains the most popular way to send and receive BTC. As of this writing, more than 54% of the existing BTC supply is stored in P2PKH outputs.
P2PKH transactions are quite similar to P2PK transactions. The most important difference is that P2PKH transactions are sent to the hash of the recipient's public key. P2PKH ultimately became more widely adopted for two main reasons. First, compared to a public key, a public key hash is a shorter and more manageable alphanumeric string. Second, P2PKH enables error detection through a checksum feature, helping users to drastically reduce the odds of sending BTC to an invalid address.
Pay To Script Hash (P2SH)
Pay To Script Hash (P2SH) was introduced as a payment type in 2012. It quickly gained support from users who wanted additional functionality not provided through P2PK or P2PKH payment types. As of this writing, nearly 31% of the existing BTC supply is stored in P2SH outputs.
P2SH transactions typically add constraints in addition to requiring an ordinary digital signature or pubkey verification. For example, a P2SH transaction may require a recipient or a group of recipients to provide digital signatures from multiple private keys. These constraints are created with a few lines of Bitcoin Script. The hash of that script is then produced as a way to lock a payment in a P2SH transaction.
There are two advantages provided by P2SH over previously-developed payment types. First, senders are able to send BTC without needing to be concerned about how recipients unlock the corresponding UTXO (e.g. via a passcode or with multi-signature requirements in place). Second, P2SH enables senders to require that recipients pay for additional network fees on transactions. Before P2SH became a standardized payment type, senders had to go through the tedious process of writing customized lines of code (known as scripts) using Bitcoin Script to achieve the same result.

Pros and Cons of the Bitcoin Protocol
Pros
- Since it was the first blockchain network ever created, Bitcoin has a first-mover advantage in the blockchain space.
- Bitcoin is listed on the vast majority of crypto exchanges and maintains a staggering daily trade volume, making it easy to buy and sell.
- Bitcoin is the world's most distributed blockchain network, which makes it practically impossible for bad actors to censor or attack.
- The network has a growing number of Layer 2 solutions, which is increasing the feasibility of BTC as a form of peer-to-peer cash.
Cons
- Unlike the Ethereum network, Bitcoin doesn't natively support robust smart contracts. This limits BTC's use as a currency for DeFi applications.
- Layer 1 scalability is limited to only around 7 transactions per second, meaning that on-chain transfers can be slow and fees can be quite high at times compared to more scalable blockchain networks.
- Crypto mining often relies heavily upon non-renewable sources of energy, which has raised public concerns over carbon emissions.
- The deflationary block rewards structure could actually be a threat to the network's long-term security since the incentive to run mining rigs is constantly decreasing.
Beyond Bitcoin - Intro To Other Blockchain Protocols
Today, Bitcoin can actually be considered a family of protocols. That’s because a number of blockchain protocols have been created as forks of the Bitcoin protocol. In many cases, blockchain protocols that originate from the Bitcoin protocol function quite differently and serve very different purposes.
Zcash, for example, is a well-known cryptocurrency project that was created using code originally written for the Bitcoin Core client. Although some characteristics between the two protocols are the same (e.g. both use the UTXO model), Zcash developers introduced several distinct features. For instance, zero-knowledge proofs enable privacy-preserving transactions on the Zcash network. Litecoin, Bitcoin Cash, and Dash are other popular examples of cryptocurrency projects that were built using the original Bitcoin Core client.
Additionally, there are many cryptocurrency projects that have been created from standalone blockchain protocols, meaning they didn’t originate from the Bitcoin protocol or from any other existing protocol. A few notable examples include Ethereum, EOS, Stellar, Tezos, Cardano, Cosmos, and Monero.
Furthermore, some cryptocurrency projects use other types of distributed ledger technologies. For example, IOTA uses a Directed Acyclic Graph (DAG) to organize transactions rather than a blockchain. For the most part, the majority of blockchain protocols were originally designed as siloed ecosystems. In other words, the Bitcoin protocol can’t easily connect or communicate with the Ethereum protocol. However, technical solutions such as atomic swaps now enable some amount of blockchain interoperability among various protocols.
Hold and Trade BTC On AtomicDEX
AtomicDEX is a non-custodial multi-coin wallet and atomic swap DEX. Store Bitcoin as well as Etheruem, Binance Coin, Dogecoin, and many other coins in your own wallet. When you're ready to trade, AtomicDEX supports cross-chain swaps. Your keys, your coins.




